Detecting Honeypots via 'Flawed Logic' issues
Novel ways to detect the most popular open-source honeypots (and automate the detection process with Nuclei).
Recently at Ekoparty and SwissCyberStorm I presented novel ways to detect the most popular open-source honeypots such as ADBHoney, Conpot, Cowrie, Dionaea (multiple services), ElasticPot, Mailoney, Redis Honeypot, Snare, among others. Here the summary and presented materials in case you missed it.
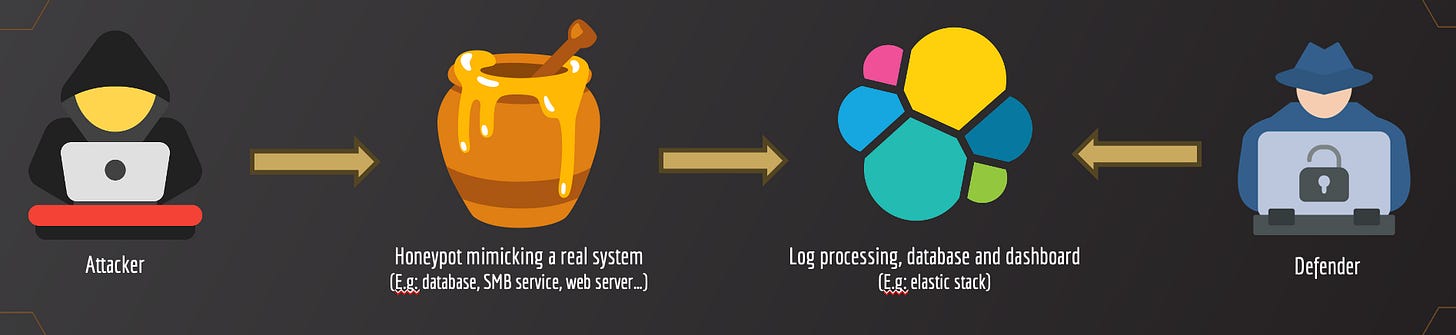
WHAT IS A HONEYPOT?
A honeypot mimics a real system - that can be vulnerable on purpose - to attract attackers and study their TTPs (Tactics, Techniques and Procedures). This is typically done to gather intelligence, attacks statistics, discover new threats and improve the detection systems.
COMMON DETECTION TECHNIQUES
Over the years, security researchers have published different techniques to identify honeypots. Most previous work is based on analyzing the following stuff:
Default services banner
(E.g.: 220 mailrelay.local ESMTP Exim 4.81 #1 Thu, 29 Jul 2010 05:13:48 -0700)Default response to commands
(E.g.: cat /etc/passwd shows user “Phil California”)Certificates configuration
(E.g.: Organization issuer/subject: “dionaea.carnivore.it”)Suspicious number of open ports in the host
(E.g.: All ports are open)Suspicious hosting provider
(E.g.: ICS honeypots on Cloud hosting)
MY RESEARCH
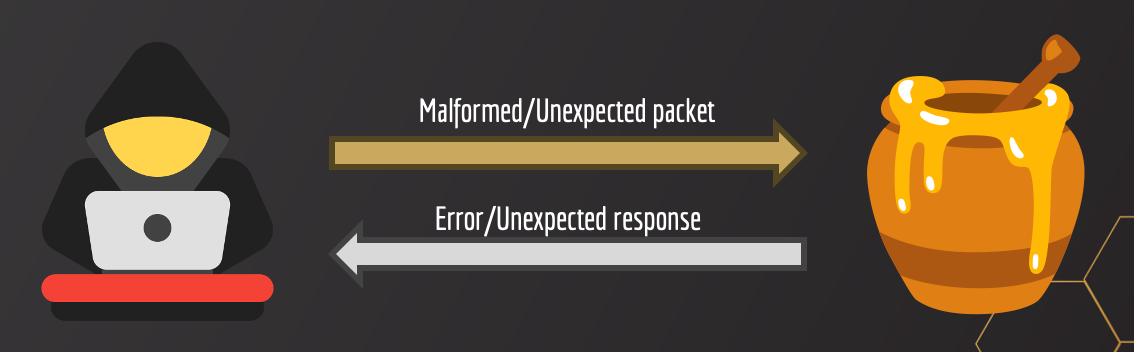
I aimed to detect honeypots by abusing a flawed logic in their network packet-handling functions. How? We send a malformed or unexpected network packet to the honeypot and, in case of a flawed logic, it will reply with an error or an unexpected response. We will use such a reply to identify the honeypot.
Why this way? Because this detection mechanism can bypass the countermeasures implemented to avoid the identification methods revealed by previous work. In other words, regardless of whether the banners, certificates, or command's static outputs are customized, we can still detect the honeypot due to the flawed logic issue. This represents a sort of bug that would require patching the honeypot's code in order to fix it, a process typically more complex.
In this research, I also limited my focus to finding a flawed logic issue in the first or second interaction with the honeypot. This was to minimize interaction with the honeypot and enable large-scale analysis for honeypot detection in a fast and efficient way :)
HONEYPOT’S FLAWED LOGIC
I analyzed about 15 of the most popular open-source honeypots and found a flawed logic in all of them. I will describe two examples here to give you an idea of how this detection technique works, and then you can find all the rest in the materials section at the end of this post.
SNARE
Snare is an HTTP (Web server) honeypot.
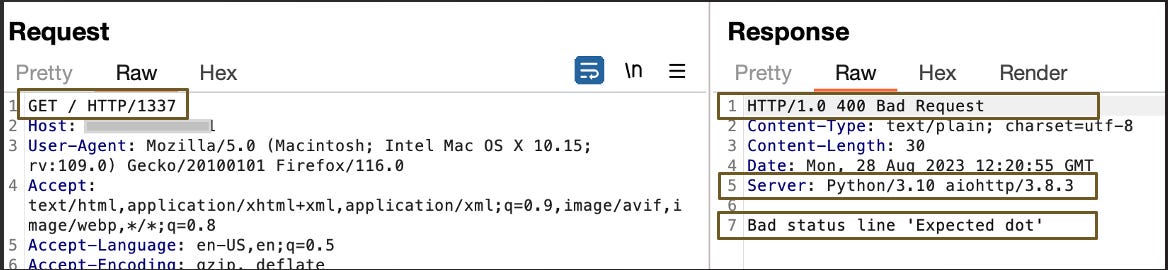
If we send the following HTTP request with a wrong HTTP version:
GET / HTTP/1337
The honeypot replies with the following error generated by the Python script:
Bad status line ‘Expected dot’
Example:
A suspicious banner can also be observed. However, since banners are customizable, I recommend basing the detection on the flawed logic.
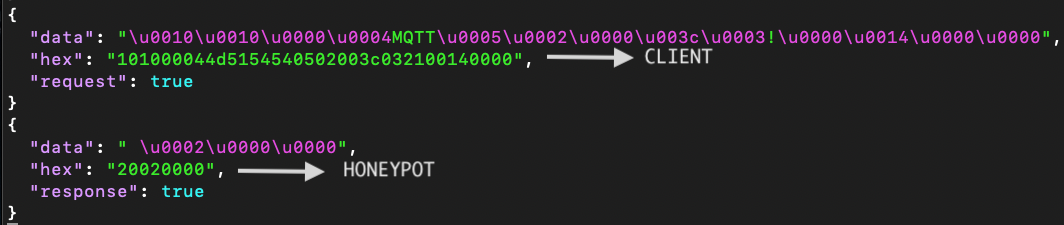
DIONAEA MQTT
A Mosquitto honeypot, part of the popular Dionaea suite.
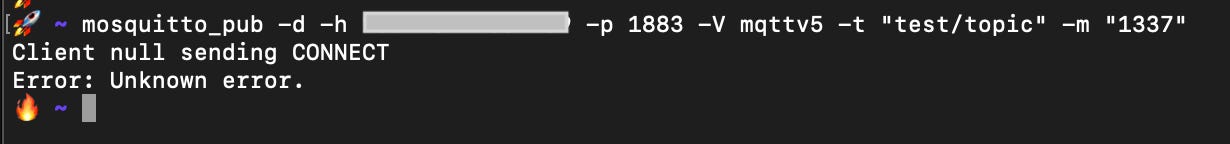
If we send a v5-format packet (publisher), the honeypot responds with a v3-format packet (susbcriber).
Let’s see how this looks like on the CLI:
If we send a '-V mqttv5' packet to the honeypot, it responds with an unexpected packet for the publisher (mqttv3-format), and the client reports an error.
Below we can observe the network packets exchange:
We can use the flawed replies from the honeypots to identify them.
AUTOMATION
As mentioned, above are just two examples. I discovered flawed logic issues in all the popular open-sources honeypots I analyzed. In order to facilitate and automate the detection, I created about 15 Nuclei templates, one for each honeypot.
Github repository of the templates: UnaPibaGeek/honeypots-detection.
Usage:
Nuclei has already merged these templates to their official templates repository. So you can update your Nuclei installation and use them from there.
Presentation slides (counter-intelligence slides were removed here): Honeypots Detection via Flawed Logic Issues.
If any question, do not hesitate to reach me out.
Sheila A. Berta (@UnaPibaGeek)